
SS7: The necessity and also a Major Cybersecurity Concern
Explore the cybersecurity challenges facing space technologies, drawing examples from real-world events. From securing satellite communications and ground stations to the risks posed by legacy systems in orbit, the article dives deep into the unique vulnerabilities and defense strategies required for space assets.

Cybersecurity Implications of Space Technologies : A Deep Dive
Explore the cybersecurity challenges facing space technologies, drawing examples from real-world events. From securing satellite communications and ground stations to the risks posed by legacy systems in orbit, the article dives deep into the unique vulnerabilities and defense strategies required for space assets.

Cybersecurity Implications of 5G Networks: A Technical Deep Dive
D
ive deep into the unique vulnerabilities and potential attack vectors associated with 5G networks. Explore how we can safeguard this game-changing technology and ensure a secure future in our increasingly connected world.

Cybersecurity in Autonomous Systems: A Technical Exploration
I explored the technical challenges and solutions involved in securing autonomous systems. From sensor integrity and machine learning attacks to secure communication protocols and real-world case studies, this deep dive covers the strategies that keep these advanced systems safe from cyber threats.

Dark Web: A Technical Deep Dive into Monitoring and Intelligence Gathering
Take a technical deep dive into the world of dark web monitoring and intelligence gathering. From understanding the underlying technology to deploying advanced tools for threat detection, this piece explores the detailed steps and strategies that cybersecurity teams can use to stay ahead of potential threats.
Threat Intelligence and APTs: Understanding and Mitigating Persistent Cyber Threats
Explore the world of APTs and the vital role of Threat Intelligence in defending against these persistent threats. From real-world examples to advanced mitigation strategies, this piece is packed with insights for cybersecurity professionals and anyone concerned with protecting critical systems.

IoT Security and Vulnerabilities: Navigating the Risks of a Connected World
Delve into the key factors contributing to IoT vulnerabilities, explore common attack vectors, and shared advanced strategies for safeguarding these critical devices. Whether you're involved in cybersecurity, IT, or IoT development, this is a must-read.
Cybersecurity in Critical Infrastructure: Safeguarding the Backbone of Modern Society
Explore the unique cybersecurity challenges faced by critical infrastructure, from legacy systems to the integration of operational and information technology. I dive into advanced strategies, such as threat detection, network segmentation, and supply chain security, to help safeguard these essential assets.
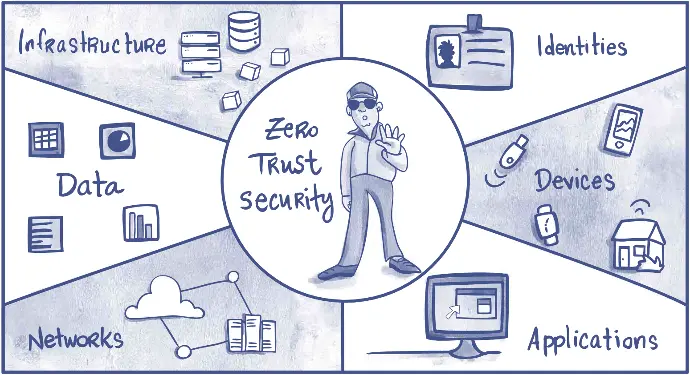
Zero Trust Architecture: The Future of Cybersecurity
Explore how Zero Trust Architecture can transform your approach to cybersecurity, covering key components like Identity and Access Management, Micro-Segmentation, and more.